When it comes to the online safety of a business, there’s a series of steps companies can take to protect their team, customers, and data.
Having robust defences in place is key, but it’s important for businesses to stay clued in on what type of attacks they’re vulnerable to, what these scams look like, and how to prevent them.
One of the most effective and worrying cybercrime tactics used today on businesses of all sizes is spear phishing. We’re going to give you the rundown on how this calculated and sophisticated cyberattack works, how to spot it, and how to mitigate the risk.
Spear phishing
Spear phishing in contrast to regular phishing, takes a more targeted approach rather than targeting a large volume of people. Spear phishing singles out an individual or organisation.
Hackers are acutely aware that by targeting an individual, or a group of individuals, they must make the email, text, or phone call almost impossible to spot as a threat. This is where hackers get creative and research their victims to create personalised scams. This level of attention to detail increases the perceived validity of the email and the chances of a successful breach.
The main goal of spear phishing is to trick people into revealing sensitive information, downloading malware or ransomware, or process unauthorised payments set up by the hacker. So, how does it work?
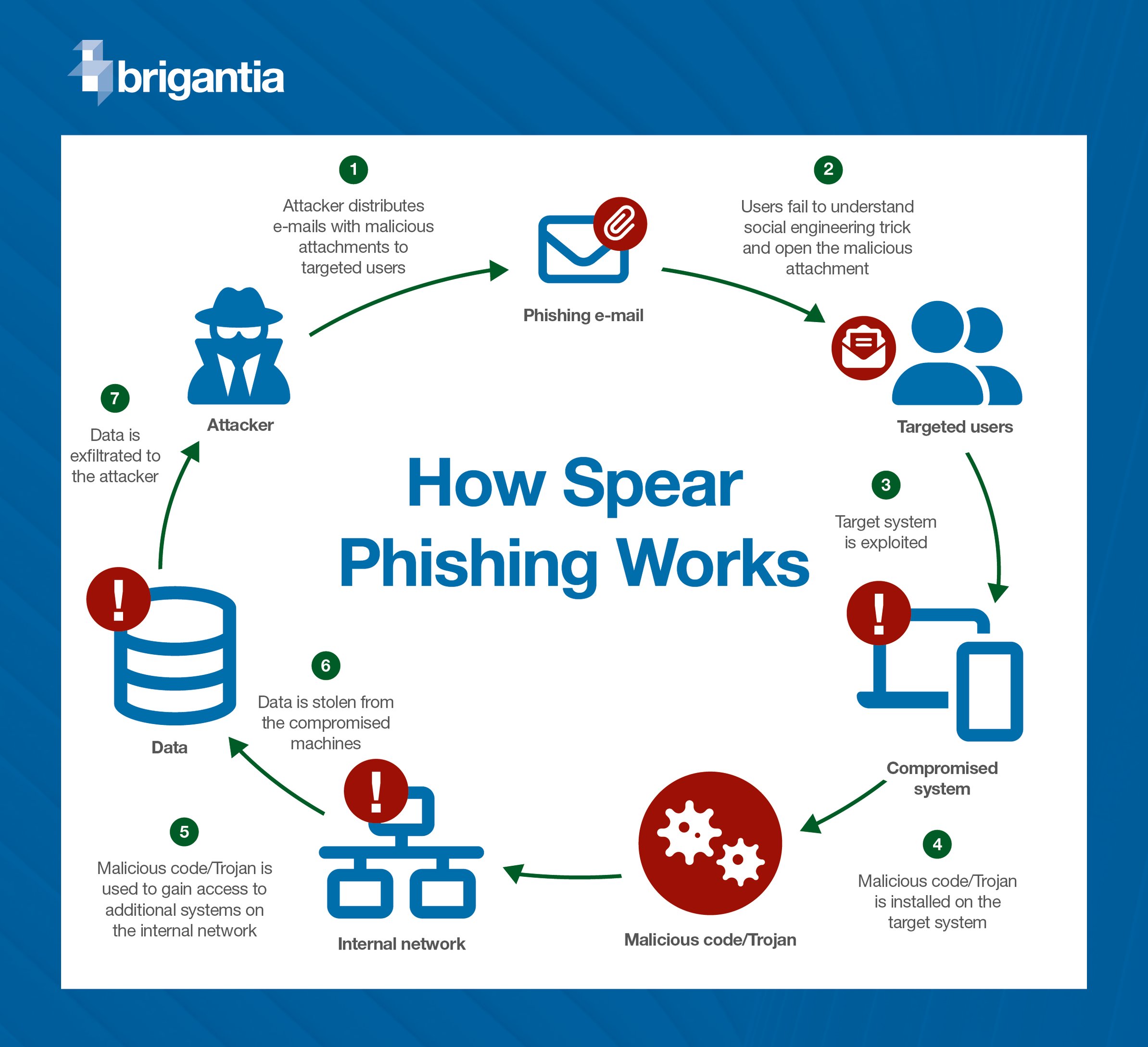
How spear phishing works
When we look at a vast selection of hacking attempts and cybercrime activity, social engineering is a popular strategy used by cybercriminals.
Social engineering is the psychological manipulation used to pressure the target into performing an action that serves the hacker’s objective. In the context of spear phishing, hackers will often impersonate high-ranking or senior members of staff, manipulating employees, either through guilt or through perceived repercussions from ignoring requests from their superior.
There are a series of steps to a spear phishing attempt, and we’re going to break these down one by one.
Step 1: Attacker distributes emails
Phase one of the attacker’s operation. An email with malicious content and attachments, are sent to a targeted victim(s).
Step 2: User opens malicious attachment
The targeted audience fails to detect the social engineering trick, opening the malicious attachment.
Step 3: The target’s system is exploited
The attacker gains access to the user’s system and begins to exploit it.
Step 4: Malicious code and trojans are installed on the system
Now the attacker has access to the target’s system, they begin to install malware and trojans, which will act as the key to infiltrating IT systems and stealing sensitive information.
Step 5: Attacker gains access to the company’s network
After successfully installing the malicious code, the hacker can then use this to gain access to additional systems on the internal network.
Step 6: Data is stolen from compromised machines
The machines, network, and IT infrastructure are now compromised, and the hacker begins to steal sensitive business data.
Step 7: Data is exfiltrated to the attacker
The hacker, or attacker, exfiltrates data from company machines.
What to look out for
Spear phishing emails can often be difficult to spot. This is largely due to the extensive effort put in by the attacker to make the spam seem as authentic as possible.
Attackers may try to impersonate a sender’s identity. One way to ascertain the authenticity of the sender is to scrutinise the email address information. Does the email address use the official domain for the organisation? Does the email signature and company logo look legitimate?
Hackers can be very clever with their research and their attention to detail. Sometimes, they may already be a step ahead, having hacked an individual’s email box. In this case, any emails received from the hacked email address may, on the surface, seem legitimate. If there’s ever any doubt, stop, don’t open attachments, and flag the email with the business’s dedicated IT support.
How to prevent spear phishing - what can I do to protect my business against spear phishing?
To avoid becoming victims of sophisticated spear phishing attempts, employees need to feel confident in being able to spot suspicious emails.
It’s also imperative that businesses are vigilant when reading email content, keeping a particular eye on user language. Any urgent requests to send money to an unfamiliar bank account or mobile number, or to fulfil tasks outside the scope of the receiver or sender’s role are a big red flag.
Having strong cybersecurity procedures in place is a strong front-line defence against potential threats. It’s particularly important for members of an organisation with access to sensitive financial or employee data, such as finance managers or HR managers, to be extra vigilant.
KnowBe4 is the largest integrated platform in the world for security awareness training blended with simulated phishing attacks and part of our carefully selected portfolio of cybersecurity vendors. KnowBe4 provides best-in-class cybersecurity training for organisations of any size, empowering teams to spot phishing attacks and remain secure.
For a strong base level of cybersecurity training, many organisations consider government-backed Cyber Essentials certification. It provides cybersecurity best-practice for a company, telling customers, and hackers, that a business takes cyber health seriously. We partner with CyberSmart for Cyber Essentials, find out more.
Final thoughts
With spear phishing attempts growing increasingly sophisticated, it’s vital that businesses have the essential policies in place to keep networks and data secure.
Taking a proactive approach to cybersecurity is the best defence against hacking attempts and ransomware attacks, and having strong in-house processes is the best place to start.
When it comes to providing cybersecurity protection, there’s a range of cybersecurity strategies available, but it’s important to remember the role that employees play in a united effort against cybercrime.
Here at Brigantia, our portfolio of vendors serve MSPs and their customers with the best cybersecurity products on the market. If you’d like to speak to one of our specialists to discuss your cybersecurity, contact our team.